What server rack project would it be without a firewall?! I got myself another bargain deal with a WatchGuard Firebox XTM25. I should have enough fun with some Stateful Packet Inspection and Threat protection (such as DoS attacks, fragmented & malformed packets, blended threats, and more), and if I manage to reactivate a WatchGuard subscription I might even get: IPS, Data Loss Prevention, APT Blocker, and a bunch of other features… 

I started to play a little with port forwarding, but couldn’t make it work, maybe I was trying to do something not quite right, so I ended up configuring a VPN in order to have access to all the internal resources. 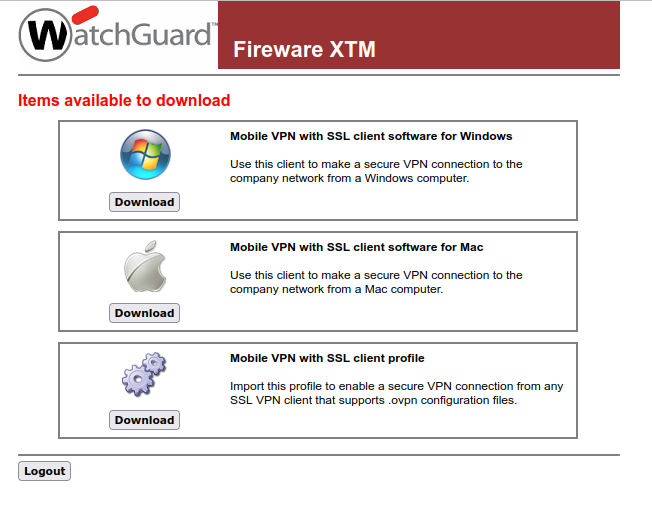
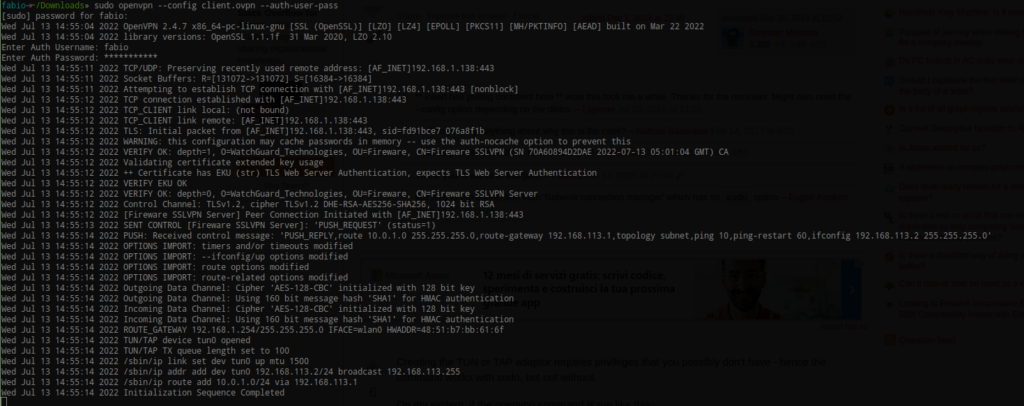
Here is my simple OpenVPN configuration:
dev tun client proto tcp remote-cert-eku "TLS Web Server Authentication" remote 192.168.1.138 443 persist-key persist-tun verb 3 mute 20 keepalive 10 60 cipher AES-256-CBC tls-cipher "DEFAULT:@SECLEVEL=0" auth SHA512 float reneg-sec 3660 nobind mute-replay-warnings auth-user-pass auth-nocache ;remember_connection 0 ;auto_reconnect 0 <ca> -----BEGIN CERTIFICATE----- OMITTED -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- OMITTED -----END CERTIFICATE----- </cert> <key> -----BEGIN PRIVATE KEY----- OMITTED -----END PRIVATE KEY----- </key>
Once connected, only internal traffic (10.0.1.0/24) is routed into the tunnel (which is super great because I believe I made a split-tunnel):
$ ip route default via 192.168.1.254 dev wlan0 proto dhcp metric 600 10.0.1.0/24 via 10.0.2.1 dev tun0 10.0.2.0/24 dev tun0 proto kernel scope link src 10.0.2.2 192.168.1.0/24 dev wlan0 proto kernel scope link src 192.168.1.164 metric 600 [...]
The next steps are configuring the firewall to shield the NAS properly. And, hopefully in the near future shield a Kubernetes cluster as well.
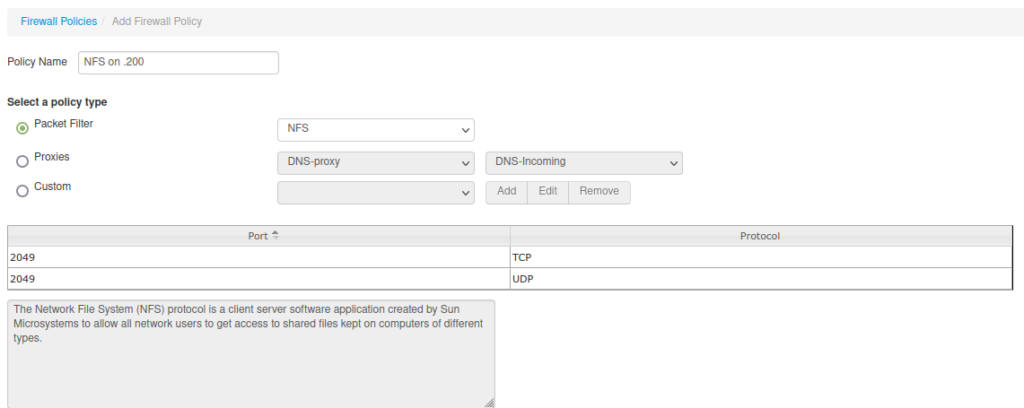
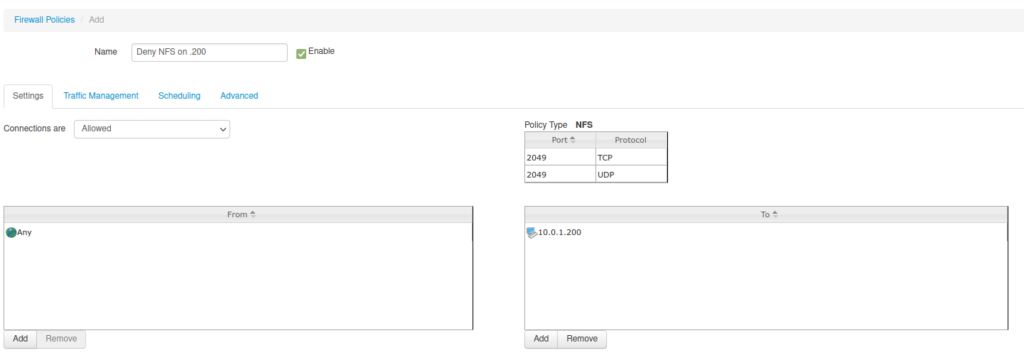
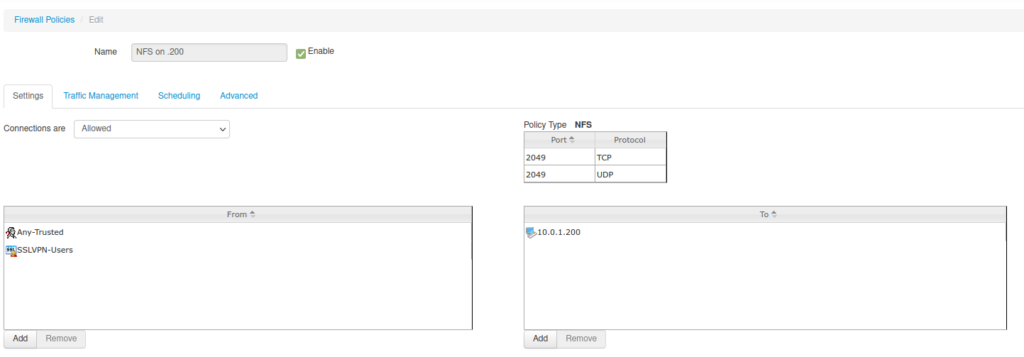
10.0.1.0/24 and 10.0.2.0/24) to the NAS IP addressSo now, I finally have a NAS, protected by my new firewall, that is accessible only from the trusted range of IP addresses (either a VPN use or a VM running in the rack). The next post will be about networking cables, and how I learned how to make one. I made lots of discoveries during this pet project!